Be Informed: Keep an Eye out for This New Phishing Scheme Attacking You Online
Beware of phishing schemes and malware.
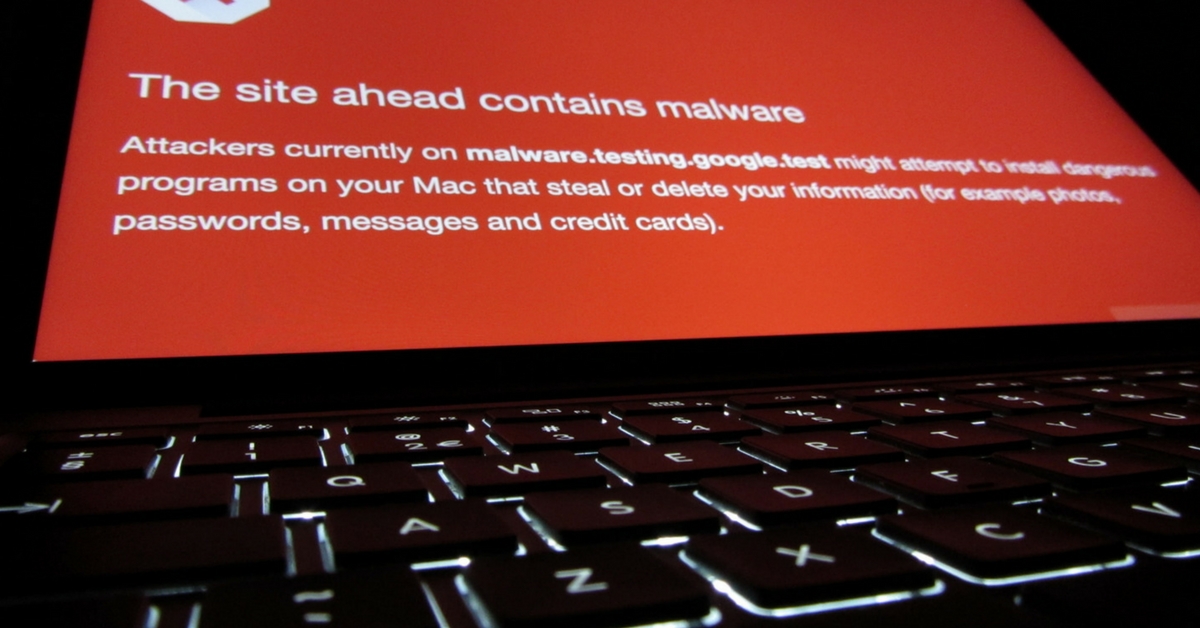
Whiling away time on the internet is fun until you unwittingly start clicking on links which expose you to hackers. Let’s face it. Your information—passwords, messages, photos, everything—is gold, for people who are targeting it. Phishing schemes net many unsuspecting users.
Out of the 24 hours in a day, you browse the internet on your phone or laptop, for 14 or 15 hours. How many hours are you vigilant? Do you always browse with an intent in mind, or mindlessly follow your trail of thoughts to open links? Do you even know how many phishing links you unknowingly click on?
Whatever your browsing behavior, hackers don’t care.

The most recent threat is Dark Caracal, a spyware campaign which is a surveillance-toolkit-for-hire. This sucks data from Android phones, and Windows machines, worldwide. Targeting 21 countries, and siphoning everything from private documents, call records, audio recordings, and text messages to contact information and photos, Dark Caracal seeks information.
Dark Caracal has been developed by the General Security Directorate, a Lebanese intelligence agency in Beirut, and is allegedly rented out to governments worldwide. It has various platforms and methods, of attacking various devices, to steal user information. Although Dark Caracal has targeted desktop users, it prioritises mobile devices as the attack vector.
For mobile phones, Dark Caracal uses custom surveillance-ware called Pallas, found in trojanized Android apps. Unaware users get tricked into installing booby-trap apps, which give malicious software a large number of permissions. Once this is done, your phone will clandestinely record audio, or provide location data, to snoops, giving them access to the phone’s entire data.
On desktops, Dark Caracal uses FinFisher, and a Windows malware called BandookRAT and also uses and a multi-platform tool called CrossRAT, for Windows, OSX and Linux devices. The application again tricks users into installing programs that seemingly have a legitimate security certificate. Once installed, this software downloads more malware from command-and-control servers. Office admins should note that the infected code can also be stashed in MS Word documents.
Dark Caracal targets a broad range of people, including, but not limited to members of the military, government officials, medical practitioners, education professionals, academics, civilians from numerous other fields, and commercial enterprises, universities, journalists, etc.
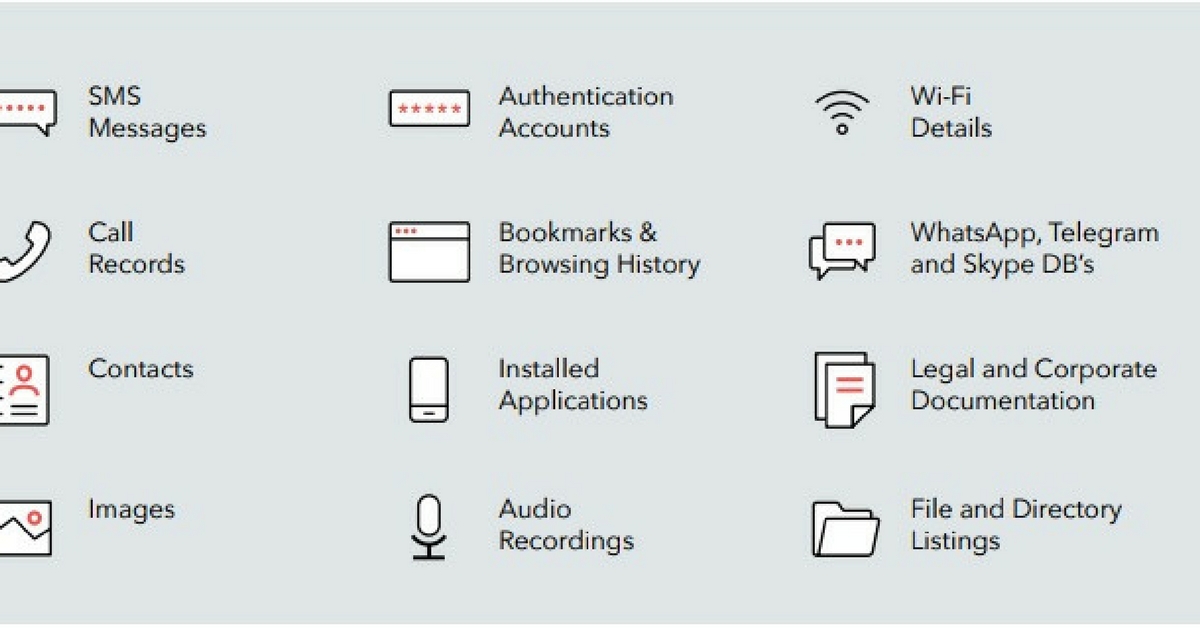
So far, Dark Caracal has managed to not only cast a wide net but also gain profound insights into the lives of its victims. The information stolen included personal messages and photos as well as corporate and legal documentation. In some cases, it was also able to paint a picture of how a particular individual spent his or her evenings at home.
How to safeguard yourself against such sophisticated cyber-espionage? What do you click, and not click on?
Stay away, and stay safe from those using phishing to mine your information.
Usually, this happens when you:
1.Click on an unspecified link;
2.Open a document;
3.Install new software on your device
4.Enter your username and password details on seemingly legitimate websites
You may also like: Be Aware: 10 Simple Things You Must Do to Protect Yourself from Cyber Thefts & Security Breaches
Once malware has been installed on your device, your phone or desktop will merely become a tool for the hackers, who can use it to do anything which includes controlling the device, spying on you and stealing information.
From accessing your contacts and sending texts to the attacker’s specified numbers to identifying nearby Wi-Fi access points and sending BSSID, SSID authentication, all of this is critical information for attackers.
As tempting or legitimate as a login page looks, don’t sign into it, because it might just be the start of one-way information exchange between you and hackers.
Like this story? Or have something to share? Write to us: [email protected], or connect with us on Facebook and Twitter.
NEW: Click here to get positive news on WhatsApp!

Similar Story

Laundromats in India? Couple Built Rs 100 Crore Biz Washing Dirty Linen Across 100 Cities
Faridabad’s Arunabh Sinha and his wife Gunjan Taneja launched UClean in 2017 to set up an organised laundromat service in India. Currently, they are spread across 100+ cities and have 350+ outlets across the country.
Read more >
If you found our stories insightful, informative, or even just enjoyable, we invite you to consider making a voluntary payment to support the work we do at The Better India. Your contribution helps us continue producing quality content that educates, inspires, and drives positive change.
Choose one of the payment options below for your contribution-
By paying for the stories you value, you directly contribute to sustaining our efforts focused on making a difference in the world. Together, let's ensure that impactful stories continue to be told and shared, enriching lives and communities alike.
Thank you for your support. Here are some frequently asked questions you might find helpful to know why you are contributing?


This story made me
-
97
-
121
-
89
-
167